LDAP Integration¶
Integration Options¶
Seldon Enterprise Platform integrates with Single Sign-On (SSO) providers for authentication.
The SSO system may also host the identities, or it may integrate to an identity provider (IdP). The IdP is often a source of truth for users across the organisation.
User details can be used for filtering/restricting visibility of namespaces. Filtering is either by user or by group.
In order for group-based filtering to be used, groups need to be available. These come from an IdP but not all IdPs support groups or support groups in integration to SSO.
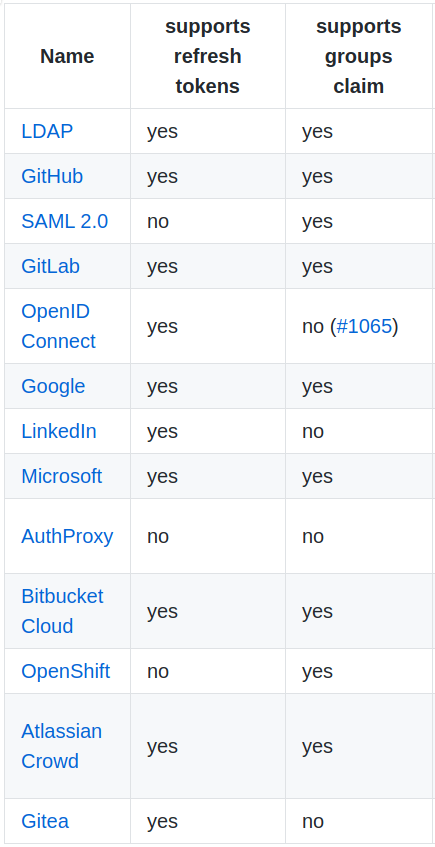
Here is a list from the Dex documentation (see their docs for latest):
If groups are to be used, we suggest integrating either keycloak or dex to LDAP. See, for example:
Or search the official documentation of those products for the latest details.
Debugging Keycloak/Groups¶
Keycloak is the most common choice at present for Identity Provider to integration to LDAP.
If configured correctly you should be able to filter namespaces by group permissions
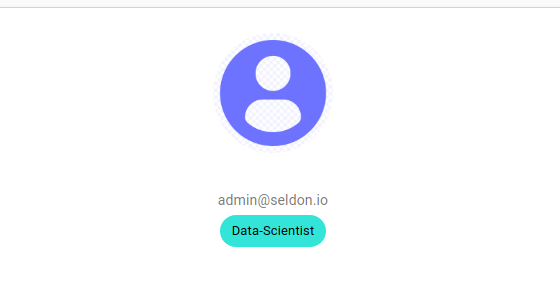
If you are not sure if groups are coming through, go to the About page in Enterprise Platform and see if a group is shown for your user. Here the group is Data Scientist:
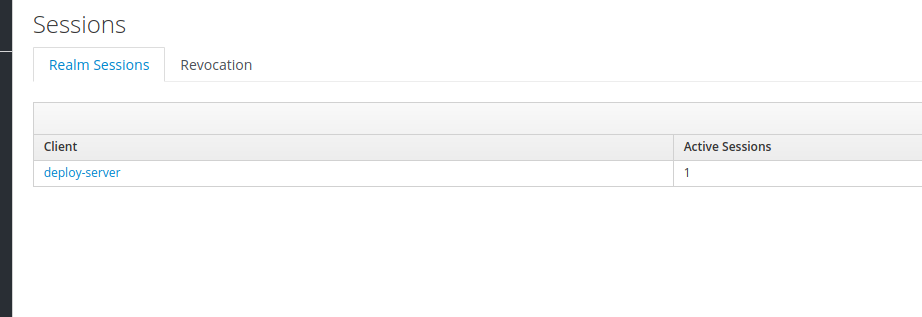
Then open another window and login to keycloak as an admin user. Go to ‘Sessions’:
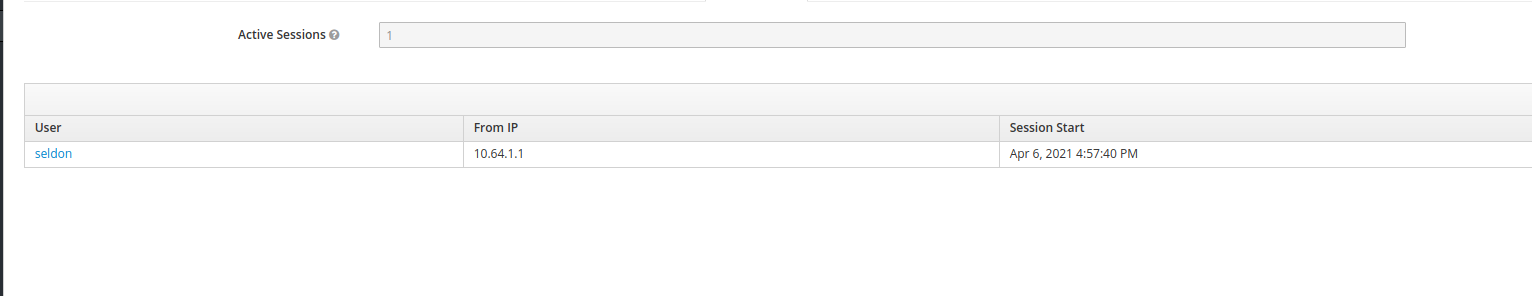
Click into the Session and click ‘Show Sessions’:
Click into that and then go to Groups:

This will tell you whether the Groups are coming through at a Keycloak level.
You can also get the full token from Seldon Enterprise Platform. To do this inspect the browser network tab with preserve logs turned out. Then logout your session. You should see a logout containing the token:
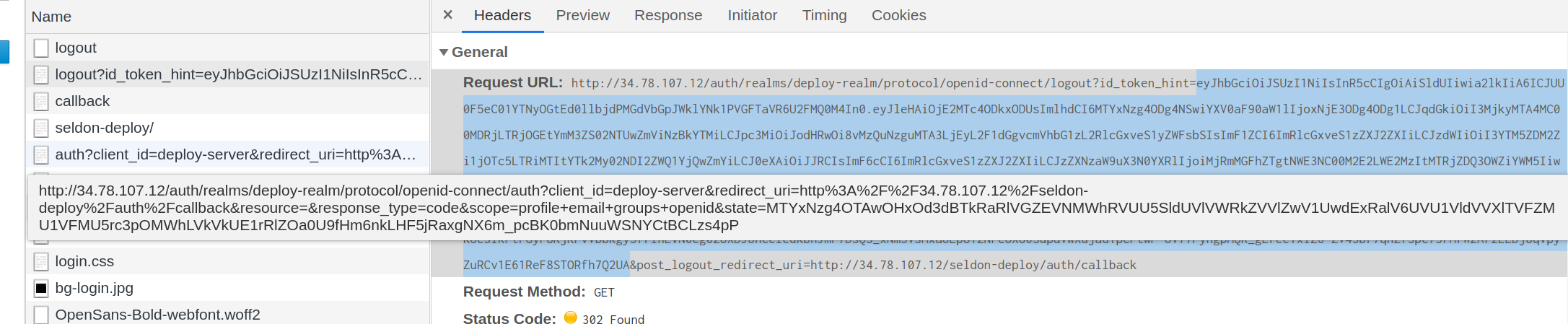
If you put the content of id_token_hint in jwt.io then you can see its contents, including groups.
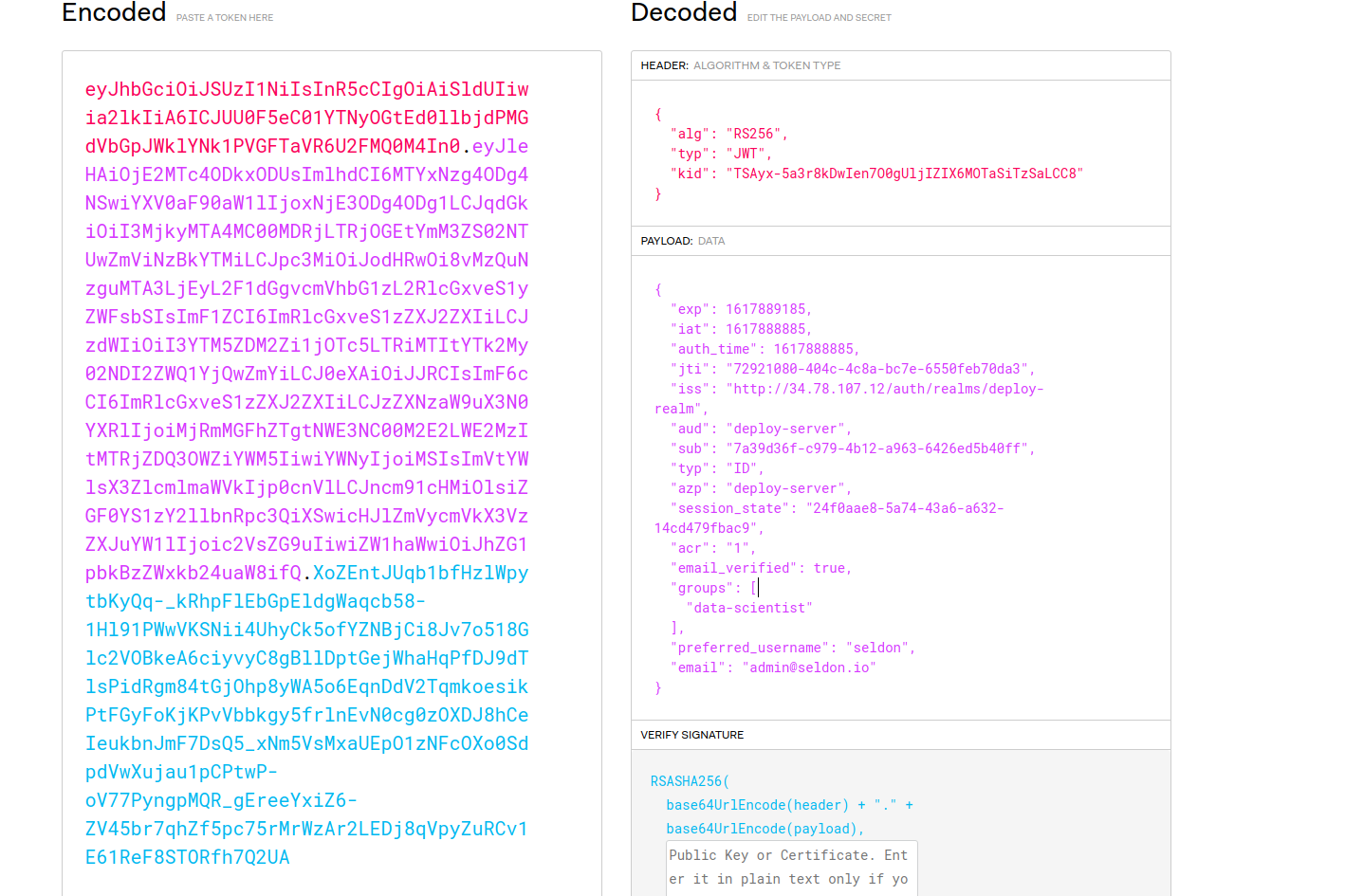
If Keycloak has the groups but the token does not, then it is likely the ‘groups’ scope is missing in the OIDC_SCOPES environment variable in the Seldon Enterprise Platform Helm configuration.
Note that there needs to be a client scope in the keycloak admin console for groups and this needs to be mapped to groups using the group membership mapper type. The scope and token claim name should both be ‘groups’. Disable ‘full group path’.
The groups scope has to be added as a client scope under the keycloak client config for the client used by Seldon Enterprise Platform.